|
|
|
Sort Order |
|
|
|
Items / Page
|
|
|
|
|
|
|
| Srl | Item |
| 1 |
ID:
100935


|
|
|
|
|
| Publication |
2010.
|
| Summary/Abstract |
Utilising a new documentary source, namely correspondence between A. K. Chesterton (1899-1973), one of the most important figures of the post-war far right in Britain, and H. J. van den Bergh (1914-1997), the head of the South African Bureau of State Security (BOSS), this article presents a case study that leads to an enhanced understanding of the nature and workings of the overseas activities of the South African security apparatus during the 1960s, its allies and its targets. The article examines and evaluates the evidence presented in this correspondence regarding the covert operations of the South African secret services against anti-apartheid activists and other exiled 'subversives' based in Britain. It will demonstrate how the South African apartheid regime operated through an ideologically aligned far right proxy to physically disrupt anti-apartheid meetings and to monitor exiled dissidents, their activities and potential sources of finance, as well as exploring how Chesterton helped to refine van den Bergh's personal intellectual framework and his definition of the who and what stood behind 'sabotage' and 'subversion' in South Africa.
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
| 2 |
ID:
100931


|
|
|
|
|
| Publication |
2010.
|
| Summary/Abstract |
This article seeks to reconcile congressional oversight models in theory with oversight realities in intelligence. For nearly three decades, political scientists have argued that Congress controls the bureaucracy - and in surprisingly efficient ways. Yet the history of intelligence oversight suggests the opposite. We take a fresh look at the logic and empirics of police patrol and fire alarm models and find that neither explains intelligence oversight well. Both rely on assumptions, such as the presence of strong and plentiful interest groups, which characterize domestic policy but not US intelligence policy. Our data - comparing committee hearing activities, legislative productivity, and interest groups across different policy domains between 1985 and 2005 - reveal that oversight varies dramatically by policy issue, and that intelligence almost always ranks at the bottom. Ironically, the same electoral incentives that generate robust oversight in some policy areas turn out to be far weaker in intelligence.
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
| 3 |
ID:
100930
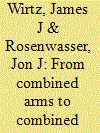

|
|
|
|
|
| Publication |
2010.
|
| Summary/Abstract |
Combined arms' operations have been a central tenet of military planning for nearly a century. They call for the integration of land, air and sea forces to achieve battlefield synergies. This philosophy has equal application to intelligence. The article advances the combined arms concept as a way to foster synergies across the intelligence disciplines - geospatial, signals, measures and signals, human, and most recently open source intelligence. It describes the strengths and weaknesses of each discipline in forming an analytical foundation for such a 'combined intelligence' and calls for developing theory to integrate the intelligence disciplines. The authors suggest that combined intelligence would confer several benefits, including more effective collection efforts and stronger countermeasures against adversary denial and deception. The article closes by calling for development of concepts and doctrine to put combined intelligence into practice.
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
| 4 |
ID:
100933


|
|
|
|
|
| Publication |
2010.
|
| Summary/Abstract |
After major intelligence failures it is often asked why intelligence and security officials failed to heed the many 'wake-up calls' that had been provided by earlier failures and surprises. This article addresses this question by examining intelligence failures as 'focusing events', which is a concept used in the literature on government policy making to explain how disasters and crises can stimulate policy change and help organizations and decision-makers learn. It argues that in order for an intelligence failure such as a major terrorist attack to inspire improved intelligence performance - to be a true wake-up call - that failure must not only act as a focusing event to bring more attention to the threat, but it must also lead to increased intelligence collection and greater receptivity toward intelligence on the part of decision-makers.
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
| 5 |
ID:
100934


|
|
|
|
|
| Publication |
2010.
|
| Summary/Abstract |
This article introduces, places in historical context and publishes selected extracts from chapter one of the Report on Colonial Security, which deals specifically with intelligence organisation both in London and overseas. Written by General Sir Gerald Templer in 1955, the report (particularly the intelligence aspects) is significant for the following reasons: it highlights the centralized and colonial intelligence failures in a particularly frank and candid manner; it details channels of communication and liaison between London and the colonies which remain classified elsewhere; and it had a substantial impact on the subsequent reorganisation and reform of intelligence in Whitehall and across the British Empire.
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
| 6 |
ID:
100932


|
|
|
|
|
| Publication |
2010.
|
| Summary/Abstract |
Continued secrecy surrounding signals intelligence during the Cold War has profoundly distorted the historical record, making a full and accurate military, diplomatic, and presidential history of the last half century impossible for now. Not only history, but the ongoing intelligence enterprise itself, would be better served by significantly greater openness. This article is adapted from the Schorreck Memorial Lecture in Cryptologic History, presented by the author at the National Cryptologic Museum, Ft. Meade, Maryland, 24 May 2010, and the National Security Agency, 26 May 2010.
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|